No issues here controlling 50+ B20X and 30+ B310-5G and some other models through Safari on latest MacOS and latest iOS/iPadOS… So must be something in your Safari settings. No extensions installed that might do something?
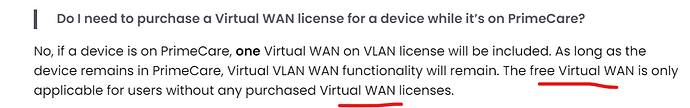
Your understanding is correct. PrimeCare device will come with One Virtual WAN feature and as long as the PrimeCare service is active, you can enjoy the One Virtual WAN feature for the device.
You only need to purchase the Virtual WAN license if you need more than 1 Virtual WAN feature ^^
Please take note of this as well :
Thank you for that clarification. Apparently the reseller I purchased the device from last Thursday was not aware of that and required that I purchase the additional license.
So weird. Only setting in safari on iPad is prevent cross site tracking. Everything else off. The thing is, it worked on previous version of the router and it’s fixed by clearing website data. So I can get it to work although with going to settings. Br1 pro max 5g
Request to add an “exclude” Client Type outbound policy option
Greetings - With all of the great new firmware features included in this release, requesting an expansion of the Client Type outbound policy to add an “exclude” option, whereas the current implementation uses an “include” option.
For example - Create a policy to have all Client Type devices on a particular network (i.e. 192.168.10.0) use an SFC tunnel, while “excluding” streaming devices (e.g. Audio & Video). This one client type exclusion option could save a considerable amount of time creating multiple, or stacked policies.
I’m eager to update my Surf Soho Mk3 to this new firmware but would like to know:
(1) What security bugs have been fixed since 8.2.1
(2) Whether the proposed rectifications proposed by @Keith in response to a reported security breach (see here: Peplink | Pepwave - Forum) have been implemented in this 8.3.0 firmware? If so, please confirm which issues have been addressed within the formal statement noting that some rectifications indicate a fix in EITHER 8.3.0 or 9.0.
(3) Is In Control enabled by default in firmware 8.3.0? If so is there an option to turn it off?
Thanks in advance for your reply…
- https://download.peplink.com/resources/firmware-8.3.0-release-notes.pdf
- https://download.peplink.com/resources/firmware-8.3.0-release-notes.pdf
- Yes and yes; this has always been the case.
Maybe I’m missing something… Surely you could set a rule that sends all traffic through the tunnel you want, then put a rule immediately above it that includes only the clients you want outside the tunnel, with a routing algorithm sending their traffic in whichever direction you want? Wouldn’t that rule then match for those clients, sending them outside the tunnel, with all other traffic being triggered by the next rule, which would have an algorithm presumably sending the traffic through the tunnel?
Yes, that is a valid point as well, only adding one additional policy step to the process.
I had been looking at, and intrigued by a unified, single policy rule (to reduce policies/technical overhead).
Hi Rick,
I’ve just looked over the 8.3.0 firmware notes looking for how the issues raised in the original security breach post here Peplink | Pepwave - Forum have been addressed and don’t see much, if anything of relevance.
Could you advise which “New Feature” Number addresses important issues raised by @JO3 and @PepeLeDrew such as being able to definitively disable remote access without needed to resort to firewall entries for DNS records (e.g. ac1.peplink.com and ac2.peplink.com)?
A separate but relevant clarification regarding the release notes for 8.3.0:
Regarding new feature 29630 - "[OpenVPN WAN] Fixed: Unable to save an Enforced
Outbound Policy Rule for OpenVPN WAN" I have the OpenVPN Wan licence for my Surf Soho MkIII, and it seems to reliably enforce all traffic over the OpenVPN WAN connection rather than the main unencrypted WAN (standard) connection, so does this error refer to a particular type of outbound rule that wasn’t working in 8.2.1 firmware? Does this mean that whilst running 8.2.1, the outbound rules I already have set aren’t actually being applied to traffic outbound on the OpenVPN WAN connection?
Thanks in advance for your reply…
Remote Assistance is an outbound connection. It is contacting the Remote Assistance server with ac1.peplink.com and ac2.peplink.com. It will fail to resolve the Remote Assistance server IP addresses by blocking these 2 hostnames. So, Remote Assistance will be failed to turn on at the end. Fyi, this enhancement is available in 8.3.0.
This bug - 29630 - "[OpenVPN WAN] Fixed: Unable to save an Enforced Outbound Policy Rule for OpenVPN WAN" was happened in 8.3.0 RC release. It was fixed in 8.3.0 RC5 or 8.3.0 GA firmware. You shouldn’t face this problem in 8.2.1. If you face this problem in 8.2.1, it should be different story and need to further review your outbound policies.
One small oddity with 8.3.0,
I realize Pale Moon browser is not the most common, but all of a sudden with this firmware it’s not possible to load the peplink GUI.
It gives the error:
Peer reports incompatible or unsupported protocol version
(Error code:SSL_ERROR_PROTOCOL_VERSION_ALERT)
I haven’t seen the latest version of Pale Moon have an issue on any other ssl site, but something about the new cert doesn’t seem to work with it.
Anyone else see this?
Since firmware 8.3, only TLS version 1.3 is supported for enhanced security. See item 25685 in the release notes. It is likely that the Pale Moon browser supports up to TLS 1.2 only.
Thanks very much for the reply – Pale Moon says that it supports TLS 1.3 fully and correctly. I haven’t seen this error on other web sites which are connecting via TLS 1.3, so it’s odd. The internal pepwave interface is the first and only time I’ve seen Pale Moon produce this error message.
I’ve had 2 SFE’s fail indentically after a 8.2.1 → 8.3.0 update.
After reboot, no SIM’s are detected. Reload SIM has no effect. Rebooting back to 8.2.1 everything works again.
Reverting to factory defaults in 8.3.0 brings up the cellular interfaces.
It would appear that 8.3.0 has an issue with the existing config from 8.2.1.
@Sneeze, this sounds strange… Do you mind submitting a ticket for the team to take a closer at the devices?
Do quote this forum link in the ticket as a reference.
Android router utility app not connecting to SURF SOHO after upgrade to 8.3.0 firmware
Is anyone else having issues with the Android phone router utility app after upgrading to firmware 8.3.0 ? I can no longer get the app to connect to my SURF SOHO after upgrading it from firmware version 8.2.1 to 8.3.0. I note that the description in the Google Playstore specifically states the app is for version 8.2.1, so I’m wondering if it is compatible with version 8.3.0?
I upgraded my SURF SOHO to firmware version 8.3.0 a few days ago, but I don’t remember if I used the phone app to connect to the router immediately afterward - I don’t think I did. When I did try to use the app yesterday/today, it can no longer access the router or it keeps showing that it is connecting (depending on what IP address I use in the app for “Host Name”).
In any event, I’m confused as to which IP address to use to for the router utility Host Name. I previously managed to get the utility app working with the previous version of firmware (8.2.1), but that was more of a fluke after I did some puttering around with using different IP addresses, based on the IP addresses I assigned to the SURF SOHO and my phone’s SSID (using the SURF SOHO’s browser-based configuration tool). The configuration tool also showed the WAN IP address, which is what I think I eventually used and got the router utility to connect when the firmware was version 8.2.1).
As far as I know, I’m supposed to use the WAN IP address rather than the router’s IP address or the phone’s VLAN/SSID IP address (or the phone default gateway IP). Is this correct?
I do have the web admin settings in the SURF SOHO set to be accessible using LAN/WAN and using HTTPS, and I used the same admin access port number that’s configured in the SURF SOHO, (3xxxx instead of 443) for the port number in the router utility app. In all cases, none of these IP addresses work.
Does anyone have any ideas why my phone can’t connect to the router using the router utility app?
I was pretty excited to see the new client type functionality.
But all my clients are of type “Unknown” and if i try to send feedback to client type it errors out. Error is “Update is not support at this moment”
This is from the “Client List” page. Is there somewhere else I should be setting client types? I cannot find it…
You have to connect to In Control for client types to work. You don’t have to use In-Control, just enable the connection. System (Top) → InControl (Left) → Controller (Body) … Set it to InControl and tick the box to not allow it to remotely change your settings. ![]()
Thanks - that solved my problem.