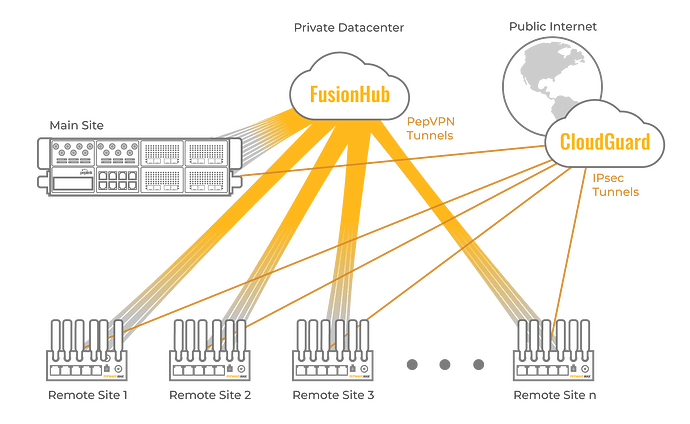
Peplink routers can simultaneously form IPsec tunnels with cloud security solutions while forming PepVPN tunnels. In these deployments, the PepVPN tunnels often connect branch offices to the company intranet while IPsec tunnels connect to the cloud security solution before accessing the public Internet.
Configuration Guide
Requirements
The example outlined below is meant for CloudGuard integration, with the requirements listed below.
-
There are 60 Remote sites, 1 “Main” site, and 1 Data Center
-
Remote sites = MAX BR1, Main site = Balance 380, DC = FusionHub
-
All the Remote sites (MAX BR1) will establish 2 types of tunnels, PepVPN/SpeedFusion to DC (FusionHub) and IPsec to CheckPoint CloudGuard
-
The PepVPN/SpeedFusion tunnel => Intranet traffic
-
The IPsec tunnel => Internet traffic
Configuration
The configuration steps illustrated below will help to redirect all the Internet traffic send to the CloudGuard via IPsec tunnel, while the traffic between the LAN subnets will be forwarded via SpeedFusion tunnel:
-
Build the PepVPN/SpeedFusion network as usual
-
Configure the IPsec profile on the MAX BR1 as follow.
- Instead of defining the default route (0.0.0.0/0.0.0.0) in the IPsec profile, you could define the IPsec - Remote Networks to exclude the Intranet range (eg. 10.0.0.0/8), an example as below:
0.0.0.1 /5 0.0.0.0 to 7.255.255.254
8.0.0.0 /7 8.0.0.1 to 9.255.255.254
11.0.0.0 /8 11.0.0.1 to 11.255.255.254
12.0.0.0 /6 12.0.0.1 to 15.255.255.254
16.0.0.0 /4 16.0.0.1 to 31.255.255.254
32.0.0.0 /3 32.0.0.1 to 63.255.255.254
64.0.0.0 /2 64.0.0.1 to 127.255.255.254
128.0.0.0 /1 128.0.0.1 to 255.255.255.254
- Sample IPsec VPN profile status as below, assuming the MAX BR1 has 2 subnets on the LAN (10.0.2.0/24, 192.168.73.0/24).
-
Note on the CloudGuard
-
Do check with CloudGuard see if it could allow how many network per IPsec connection, as we found the Zscaler only allows 8-network per IPsec tunnel (shown below).
Traffic Control and Provisioning
These redirections can be orchestrated using outbound policy. First, all traffic is configured to go through the IPsec tunnel (and hence the SWG) by default. Then, exceptions are made for intranet traffic to be sent through the PepVPN tunnels. Traffic through the VPN tunnels can then be orchestrated using outbound policy and firewall rules.
Once the PepVPN tunnels have been established, users can then apply DPI to identify each packet’s application and manage the traffic accordingly. Users can also sort traffic by IP Address, IP Network, Domain Name, PepVPN profile, or network groups. Once the IPsec and PepVPN configurations have been set on one device, uses can use InControl to push this configuration to multiple devices in the network.
Secure Web Gateway Compatibility
The application described here will also work for physical Secure Web Gateways.If the SWG is located on-premise such as in the HQ, then all traffic will head to the HQ via the PepVPN, with a breakout for Public Internet traffic that goes through the hardware SWG.