When we look to size a device for a role within a SpeedFusion WAN there are two key elements to consider, the SpeedFusion router throughput and the number of Supported SpeedFusion Peers.
You will need to do an analysis of the number of WAN connections at each location along with the available throughput, then consider any future gowth plans of that site to gauge which Balance router will be the best fit for the available bandwidth at the site.
As an example, if you had a small site using a pair of 10/12Mbps DSL connections then the Balance 210 would be fine. The 210 supports upto two WAN connections with 30Mbps of SpeedFusion throughput (you could also consider the 310 for future growth as you would have a free WAN link so you could add more bandwidth later).
However if you had a site with two 50Mbps FTTC connections then the 210 would be undersized and you would need to consider the Balance 580 (80Mbps SF Throughput) or 710 (160Mbps SF throughput) for this to make best use of the available bandwidth purely for WAN traffic.
A big element of a WAN design in the corporate environment is often web filtering. A lot of companies will have a centralised Web Proxy/Filter that they send all outbound internet traffic to that filters key categories of websites. If thats the case here, then you will definately need the bigger Balance devices as suggested above to match the SF throughput to the higher speed WAN links as all outbound internet access will need to go over SpeedFusion.
However if there is no centralized web proxy, then outbound traffic at a remote site can be split, so that internet access goes direct out over the local WAN connections and SpeedFusion is only used for site to site traffic (like VOIP and network file/web/print services). In this case a Balance 210/310 which supports 100Mbps of overall router throughput and 30Mbps of SpeedFusion VPN throughput is normally a good fit.
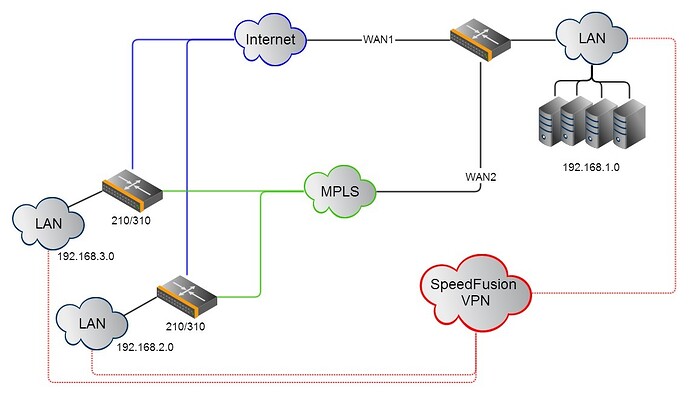
The next sizing factor is the number of SF Peers a device supports. This is the number of remote devices a single device can connect to simultaneously using SpeedFusion. A balance 210/310 can connect to two SpeedFusion Peers simultaneously and we would most often see one Peer as the main corporate datacenter and the other a a backup datacenter. A 380 Supports 20 Peers, a 580 50 peers, a 710 300 Peers etc etc (you can see the specs here http://www.peplink.com/products/balance/model-comparison/).
Obviously then, an important element of the SpeedFusion WAN design is inter-site traffic analysis. In most situations a hub and spoke WAN is fine (and preferred), with a larger enterprise device like a 580/710/1350 (or pair of devices for HA) in the Head office or datacenter (that supports the right number of SpeedFusion Peers to be able to connect to all the remote sites at the same time), and then smaller devices at the remote sites that connect back to it. In this configuration all sites can route traffic to each other via the central location as we provide dynamic route updates across SpeedFusion so that when a new site is added the exisiting sites know how to route traffic to it via the hub device.
There are some cases though, where you might want to add a direct SpeedFusion connection between the remote sites as well as having them connect to the central location. These are normally application or process based requirements. Consider for example a office location that sends large print jobs to a factory or warehouse site everyday. Print jobs tend to be bandwidth hogs, so it makes sense for that traffic to go direct between the sites themeselves rather than via the central location.
In your example of a network split across multiple countries, there will likely be teams split across these internal sites too - like marketing teams or design/CAD teams. Graphic design and CAD files can get big quick, so if they are planning to share large files (by pushing and pulling them to file servers at these locations) then connecting them together with direct SpeedFusion tunnels will reduce the bandwidth utilisation at their respective central hub locations.
In short then, without full knowledge of the client requirements I would expect this end design to consist of in country hub and spoke WANs using SpeedFusion (to keep all in country traffic local to reduce latency), with SpeedFusion tunnels between the hubs of all the countries (for VoIP traffic and other global core services like active directory / authentication). And then I would expect to see a handful of in country and global remote site to remote site SpeedFusion Tunnels added for specific traffic/application types to optimise data transit between teams.
Hope that helps, good luck with your design!
Martin