I have been using SFC for bandwidth bonding of 2 WANs but have now been blacklisted at several websites, apparently because connecting via SFC looks to them like a VPN connection and they have “no VPN connection” policies. This is a much worse problem than simple website blocking of SFC connections, such as at reddit.com, which can be undone by turning off SFC. Instead at several websites my connectivity has been blacklisted permanently. Most recently I have been locked out of my online US Social Security account because of trying to access it via SFC, which I discovered after several hours on the phone with their tech support people who were unable to tell me if I could ever be allowed access again. I had a similar problem a couple of months ago having used SFC to reach etsy.com, but was eventually able to regain access after sending several apologetic emails for “having used a VPN”. Is there a way to use SFC without it appearing to be a VPN to websites that have “np VPN connection” policies ?
It’s best to not use VPN except for use cases that specifically require VPNs. Else, put a Peplink device at your house (or one of a friend/family member) and use that to speedfusion with and egress from.
When you use the Peplink SpeedFusion Connect service (SFC), you share the same public IP with thousands of others, not just a few, so it will appear like it is being used as a public VPN.
Lots of organisations/services will now block public VPNs as they are often used to mask the identity of rouge users.
Just as those of us who are legitimate with our VPNs, some are not, and the few spoil it for the majority.
Happy surfing,
Marcus ![]()
Investigate running FusionHub Solo. You won’t be sharing the IP with anyone else and won’t have the problem you are experiencing.
We are thinking of launching a service for this exact reason, so DM me.
Running a fusionhub yourself, or using speedfusion connect relay and taking it through one of your other, better connected sites, is the answer
The only issue, running FH Solo, you still share an IP block with others. Given the IP blocks at places like AWS and Azure are assigned to them in aggregate (more often than not), others will label entire subnets as VPN blocks.
But, as Bryn and Michael said, FH Solo is 100% the best way to do this.
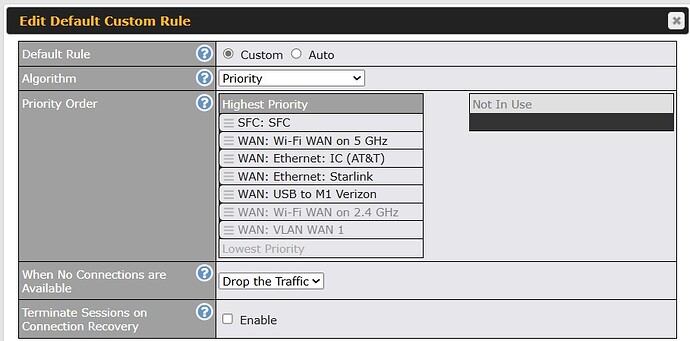
I have a very simple, quick, and no cost solution that works for us and may work for you. I have the default outbound policy to use SFC for all traffic; however, I also set up an outbound policy to exclude web traffic from using SFC. We no longer have issues with websites blocking us. Also, we have not seen any issues without SFC on web traffic since a glitch here & there is recoverable and hasn’t been noticeable after using for months now. Because of the default policy, we still have SFC for everything else which includes critical real-time applications like Zoom, VoIP, etc. Hope this helps.
Your rule just sends all traffic over WAN1, and then WAN2; this doesn’t seem to apply to only web traffic. What other rules do you have, and what order? can you show the other rules? I am having a similar problem but did the opposite; I am telling my VOIP traffic to use SFC and everything else to use WAN1, and then WAN2. But I’d prefer to do what you suggest, but I don’t see how that would work according to your screenshot, thanks!
Ryan2,
Assuming you are referring to the outbound policy I posted, let me expound on my solution. First, I set up the default outbound policy (below the added policies - easy to miss) to use SFC as the top priority. See the attached. Second, I set up policies to exclude scenarios where I didn’t want SFC to be used. The above is a policy to exclude all TCP (ie, SFC is not in the priority list). I have another to remove my Roku device because that’s just a waste of data and buffering gives me smooth video. I have a third to exclude another device that should never needs SFC.
I originally tried to do the opposite (only use SFC for Zoom, VoIP, etc) but the same protocols for Zoom seem to also be used by other non-critical video like YouTube, social media, etc. So I switched to SFC by default and excluded protocols and devices that didn’t need them. I’ve tested these and they work as intended.
Hope this helps.