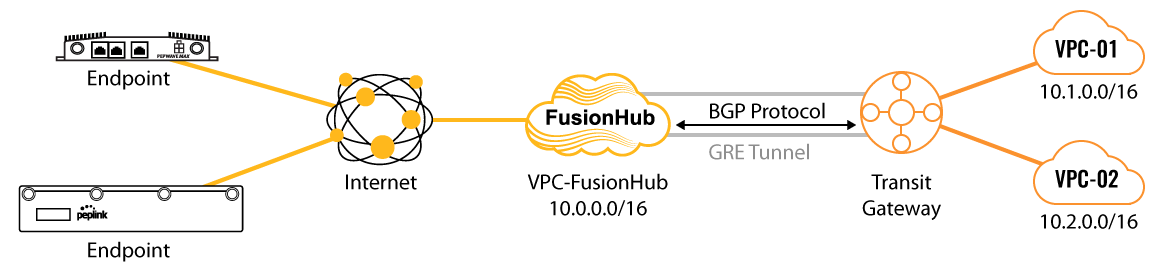
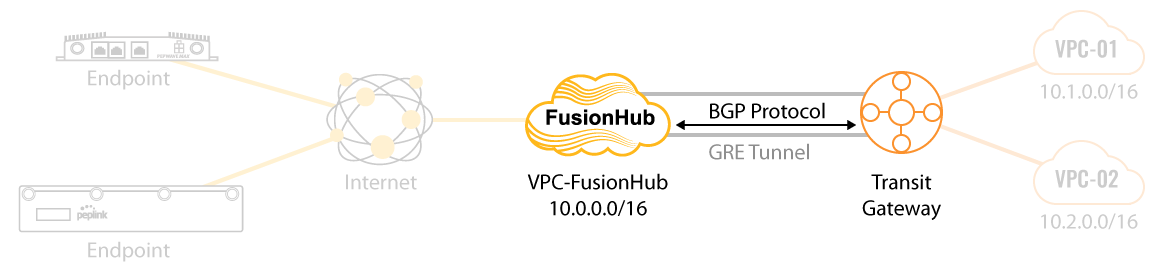
This guide walks you through the process of connecting your SpeedFusion network to an AWS Transit Gateway Connect. Here is the network we’ll be setting up:
This guide assumes you have already established the VPCs. For easier viewing, click any image to see a full-sized version.
1) Create FusionHub Instance & Install Latest Firmware (8.1.3 or above)
Set up the FusionHub instance inside the FusionHub VPC. During creating the FusionHub, manually fill in the Primary IP under Network Interface. In this example, we are using 10.0.0.10 as FusionHub IP.

After created the FusionHub, upgrade with Latest firmware.
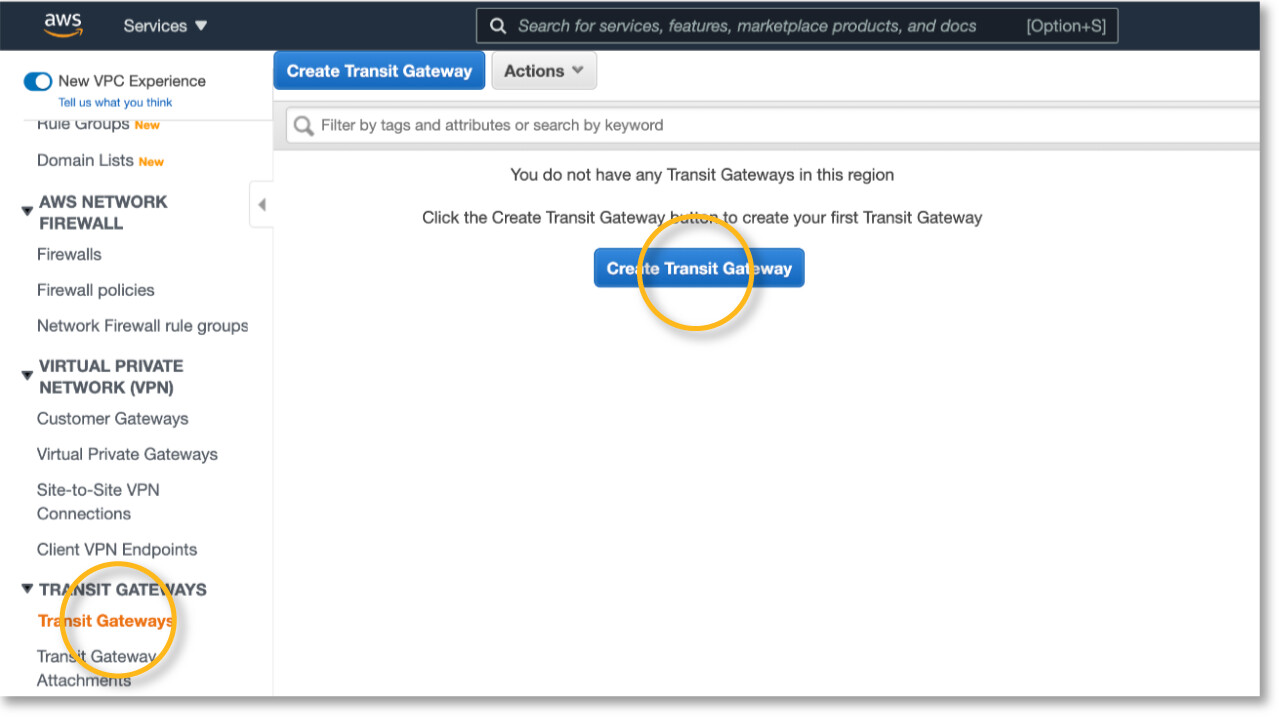
2) Create Transit Gateway and Attachments
Go to the AWS Console, navigate to VPC > TRANSIT GATEWAYS > Transit Gateway and click Create Transit Gateway
Name and configure your Transit Gateway, and then click Create Transit Gateway.
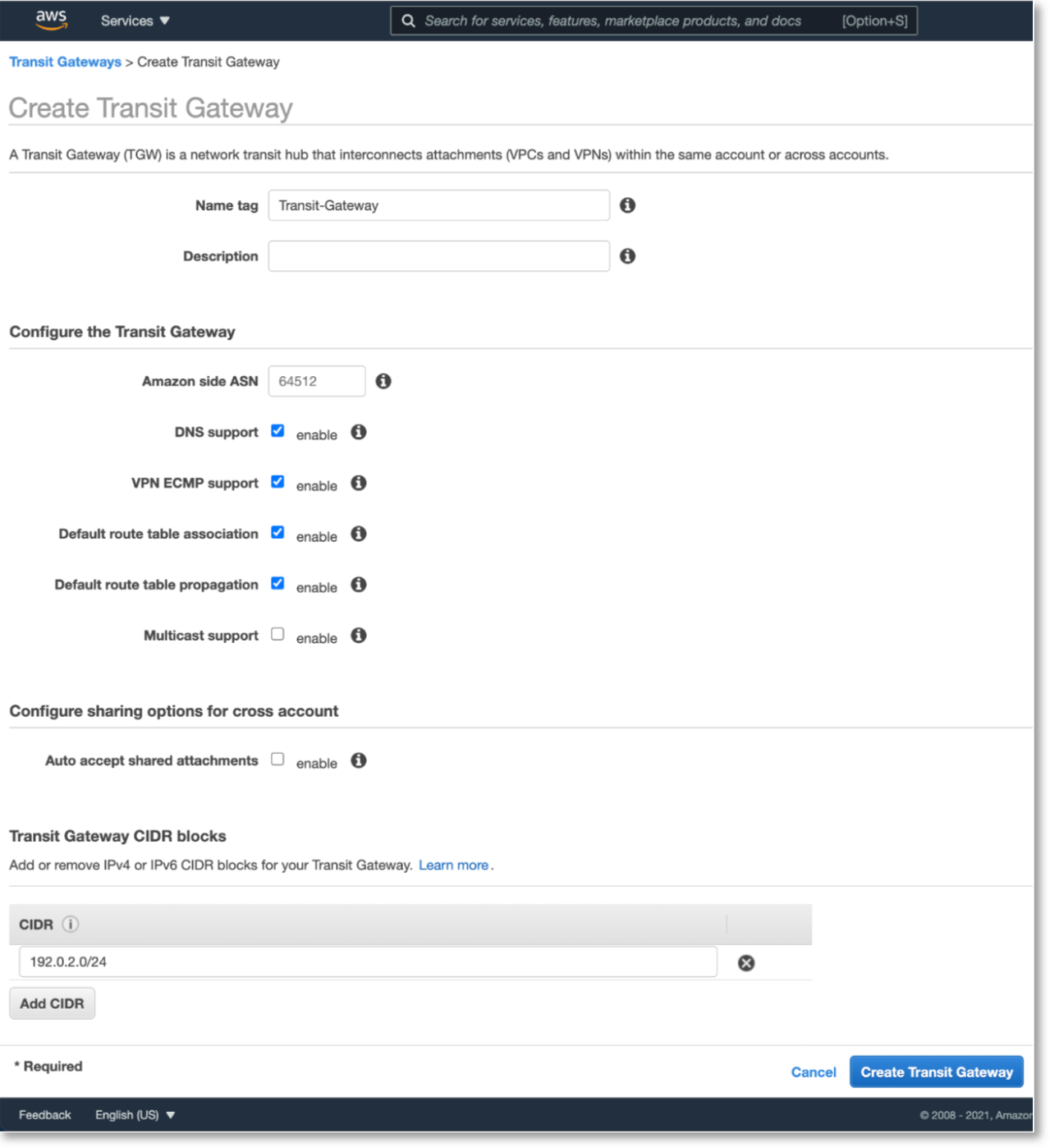
Then navigate to “TRANSIT GATEWAYS > Transit Gateway Attachments” and click Create Transit Gateway Attachment.
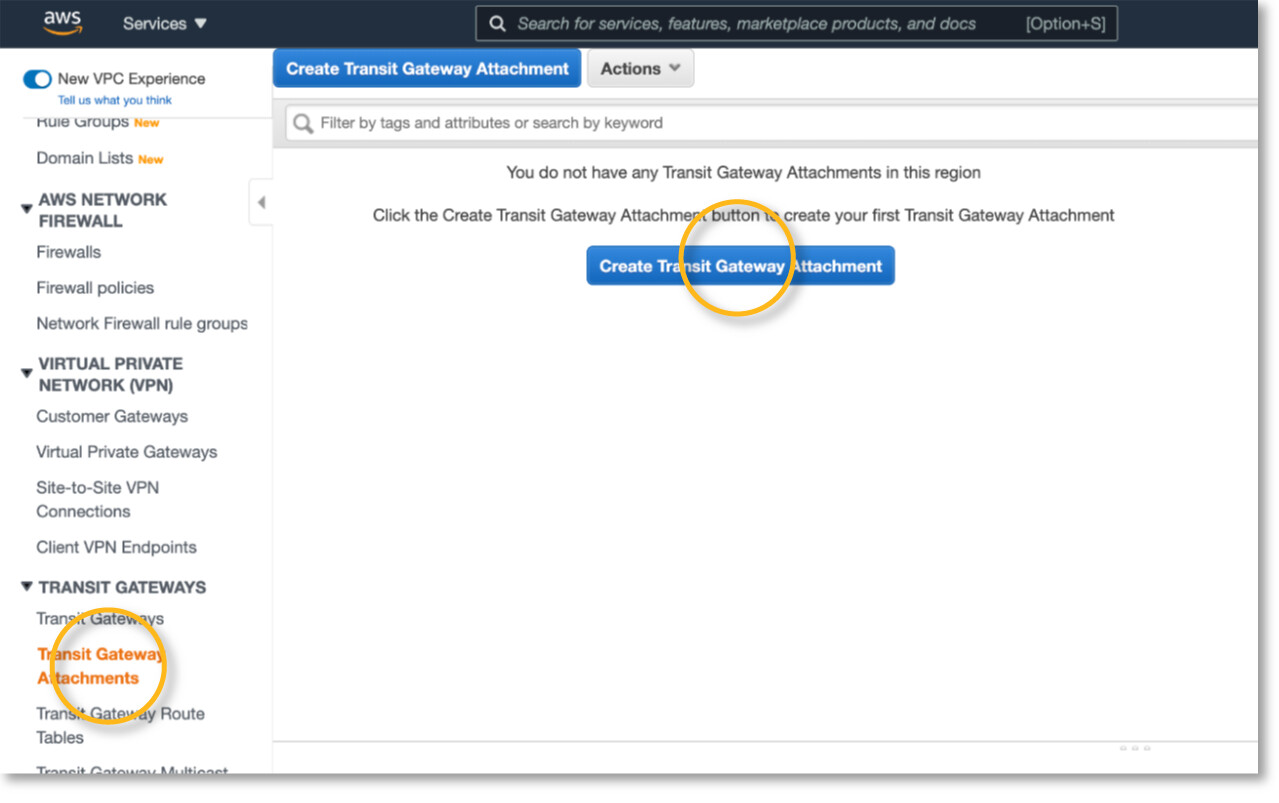
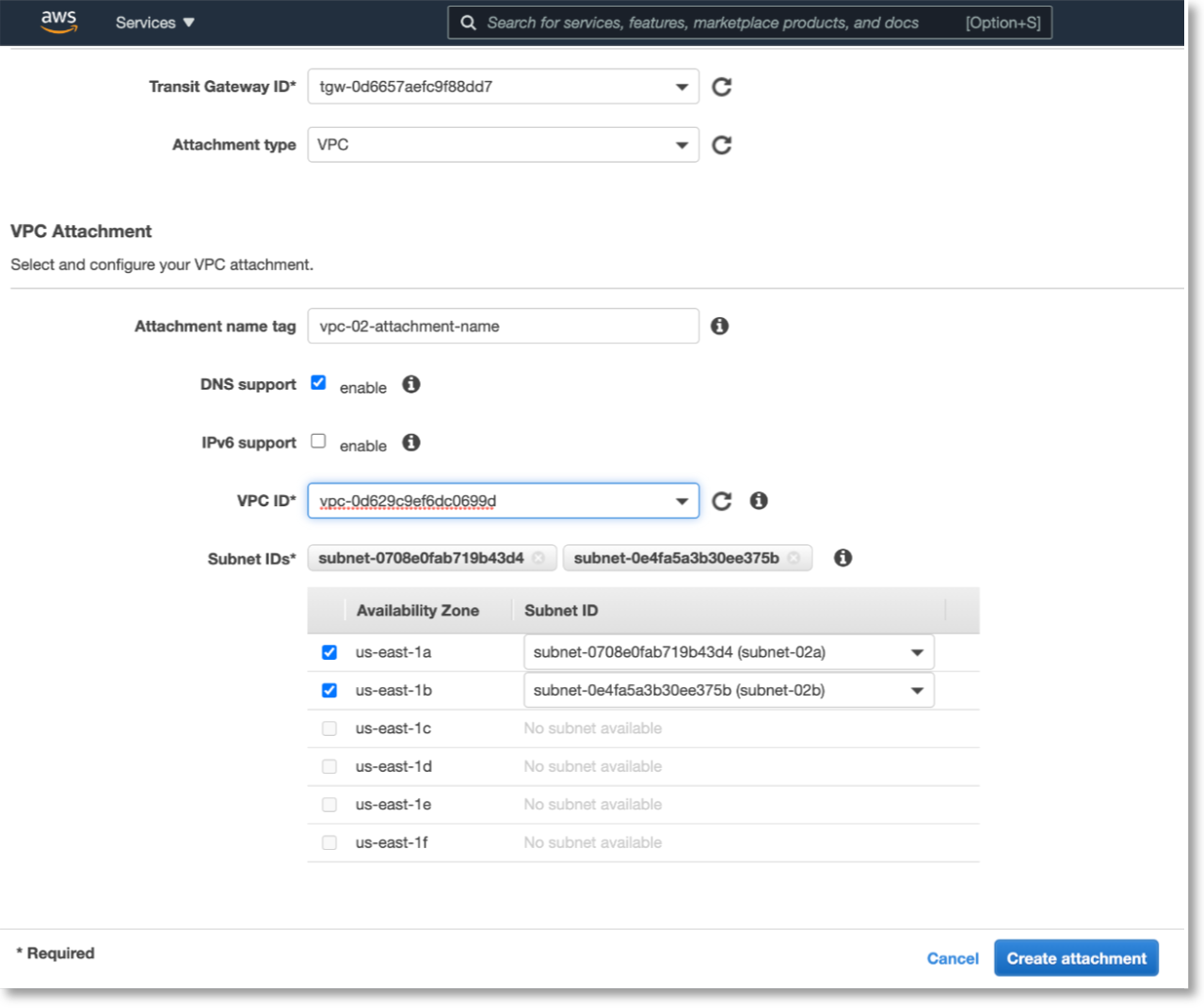
The Create Transit Gateway Attachment page will appear. From the Transit Gateway ID dropdown menu, select your new Transit Gateway. For the Attachment type, select VPC. Your VPCs will appear under VPC ID.
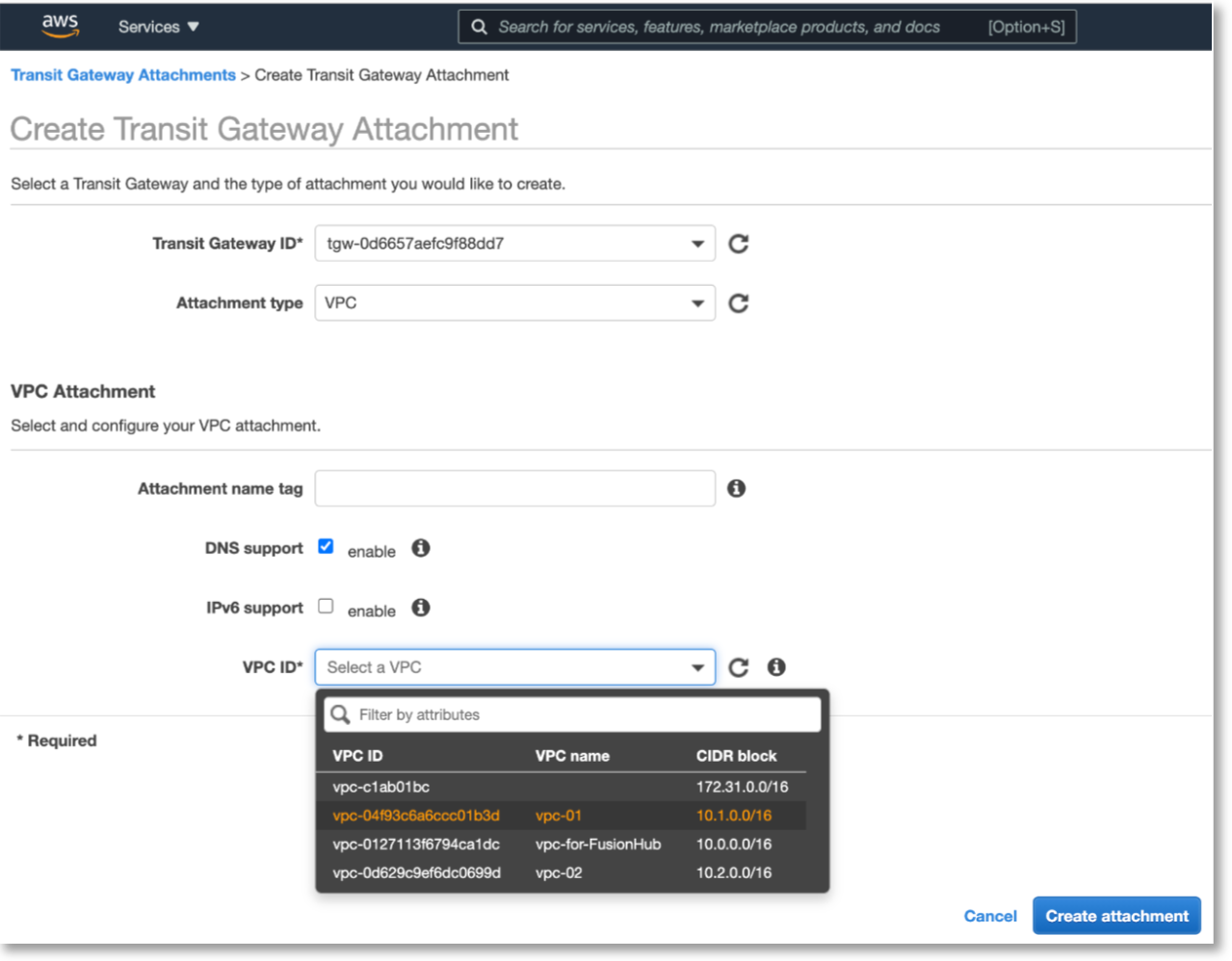
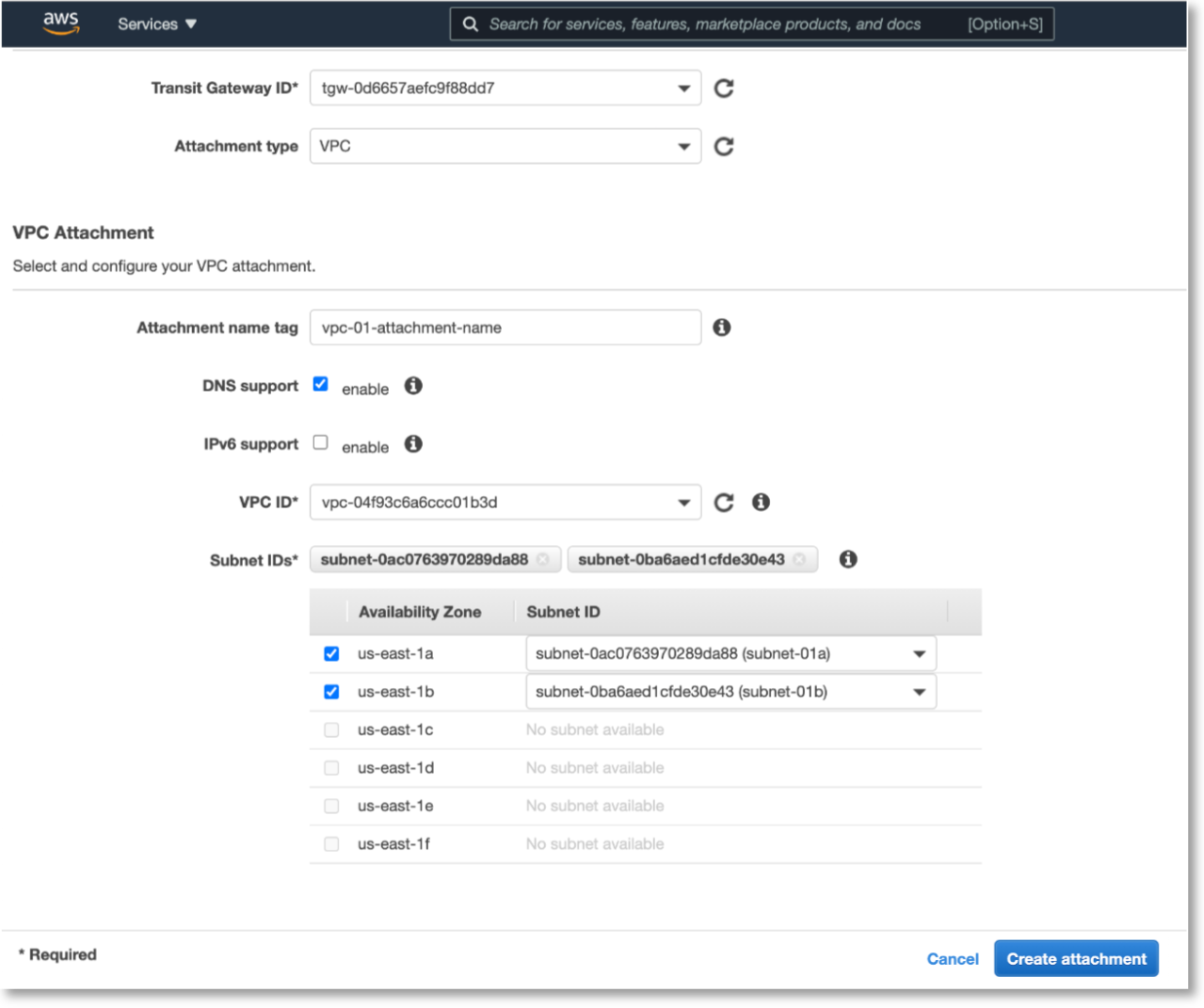
Under VPC Attachment > VPC ID, select the IDs of each VPC and select the subnets for each of them to operate in.


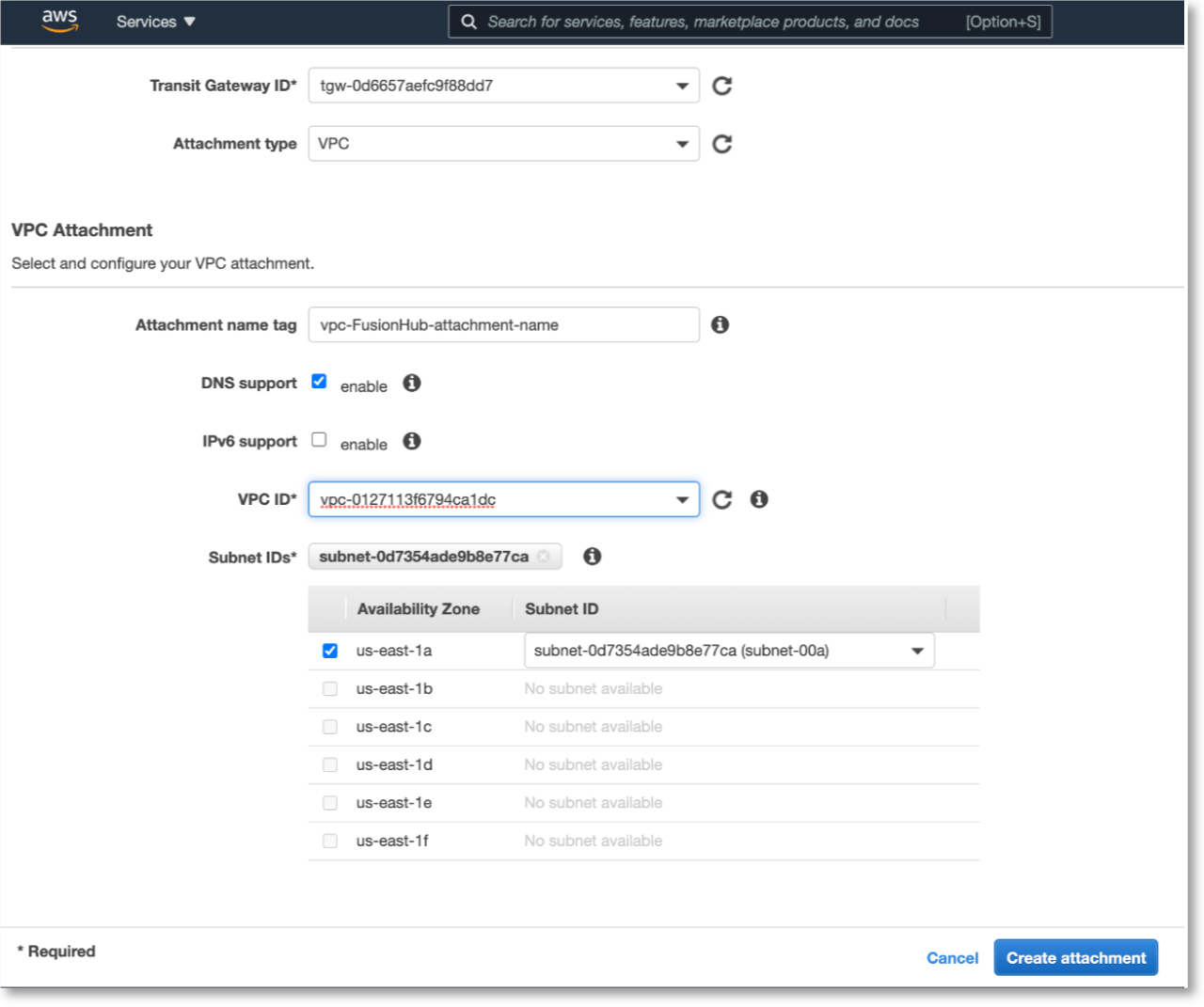
3) Connect the Transit Gateway to the FusionHub VPC
Next, create another Transit Gateway Attachment, this time with Connect as the attachment type. For the Transport Attachment ID, set it to vpc-FusionHub.
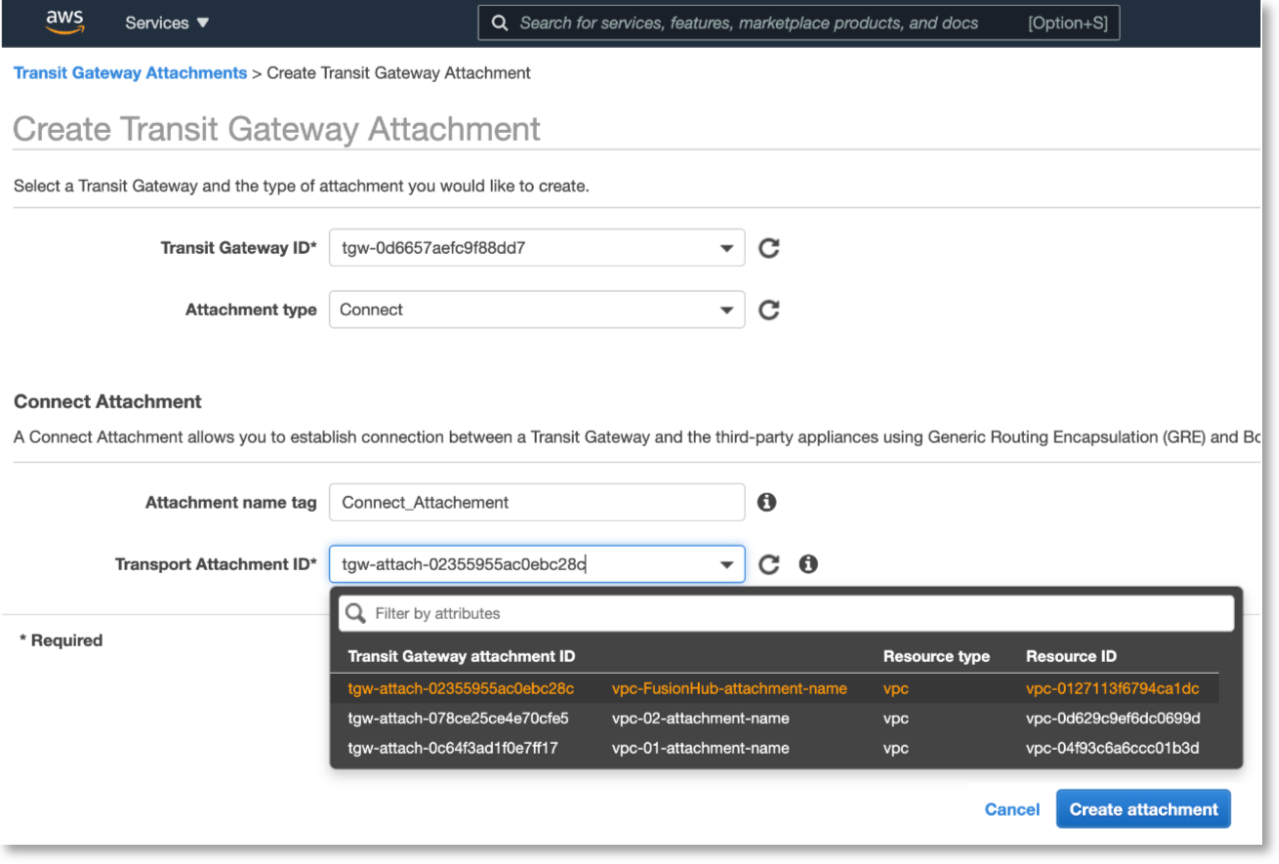
Return to TRANSIT GATEWAY > Transit Gateway Attachments, select the Connect type attachment you have just created, and on the table below, navigate to the Connect peers tab, and then click Create Connect peer
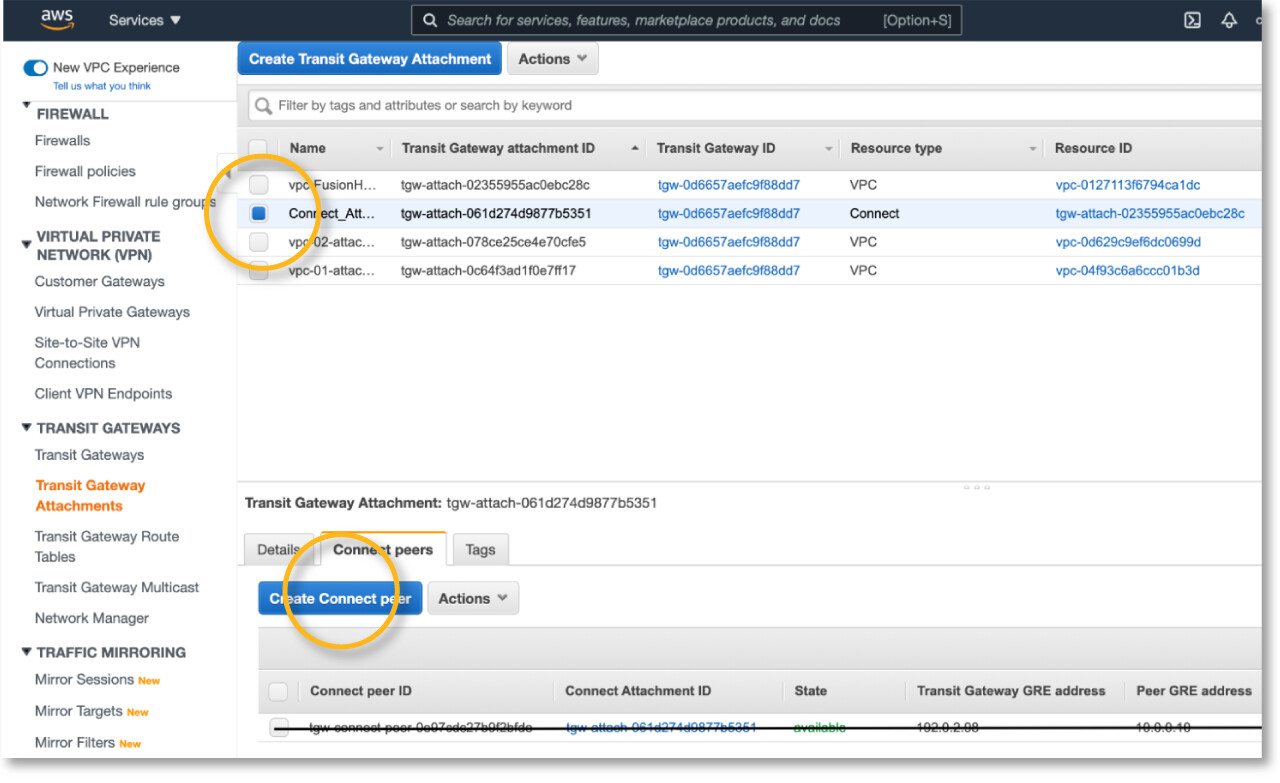
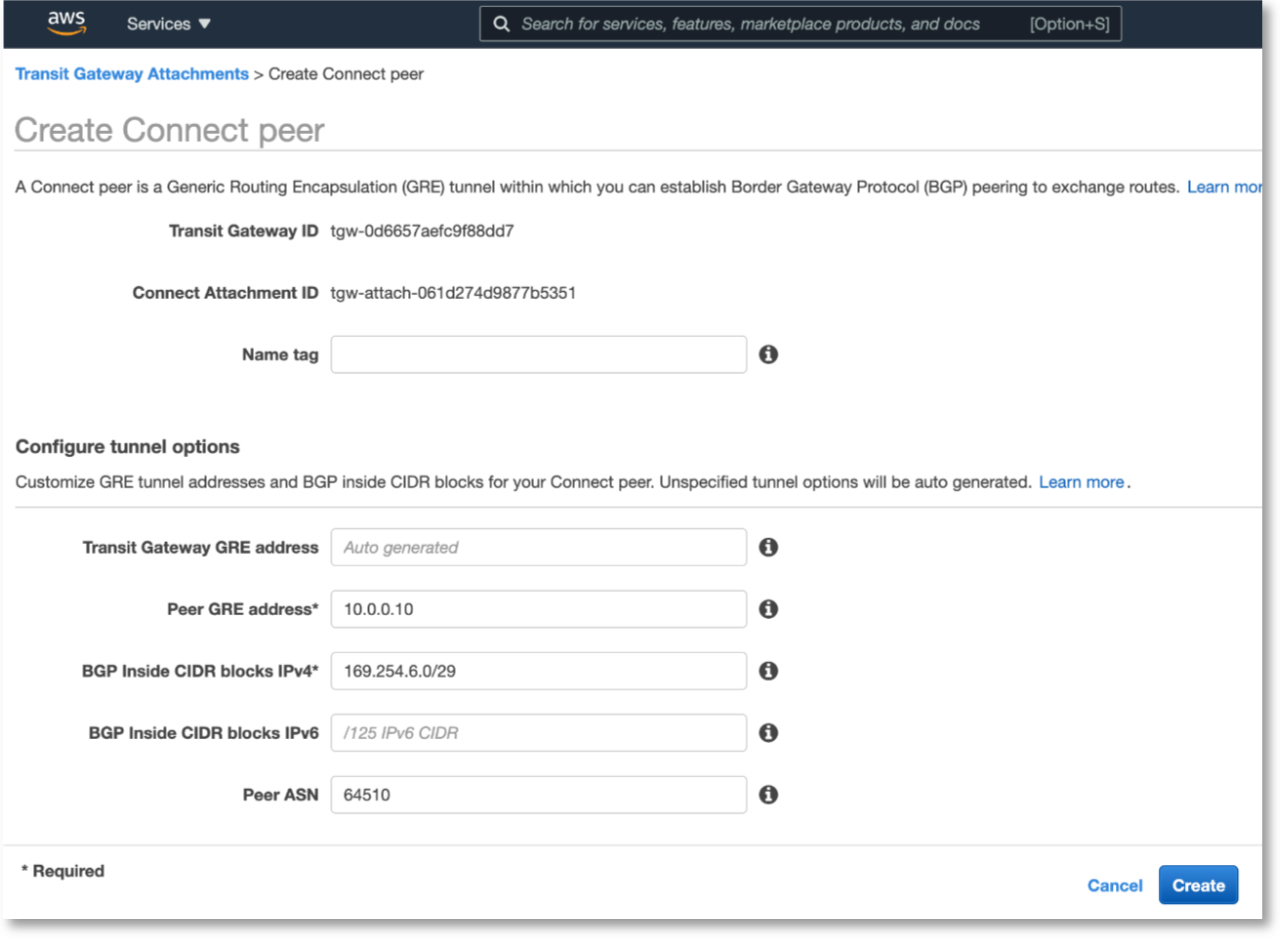
The Create Connect peer page will pop up with some info already filled. Enter the remaining information. Please fill in FusionHub LAN IP address as Peer GRE address, in this example, FusionHub IP is 10.0.0.10
4) Set Up FusionHub, GRE Tunnel, and BGP
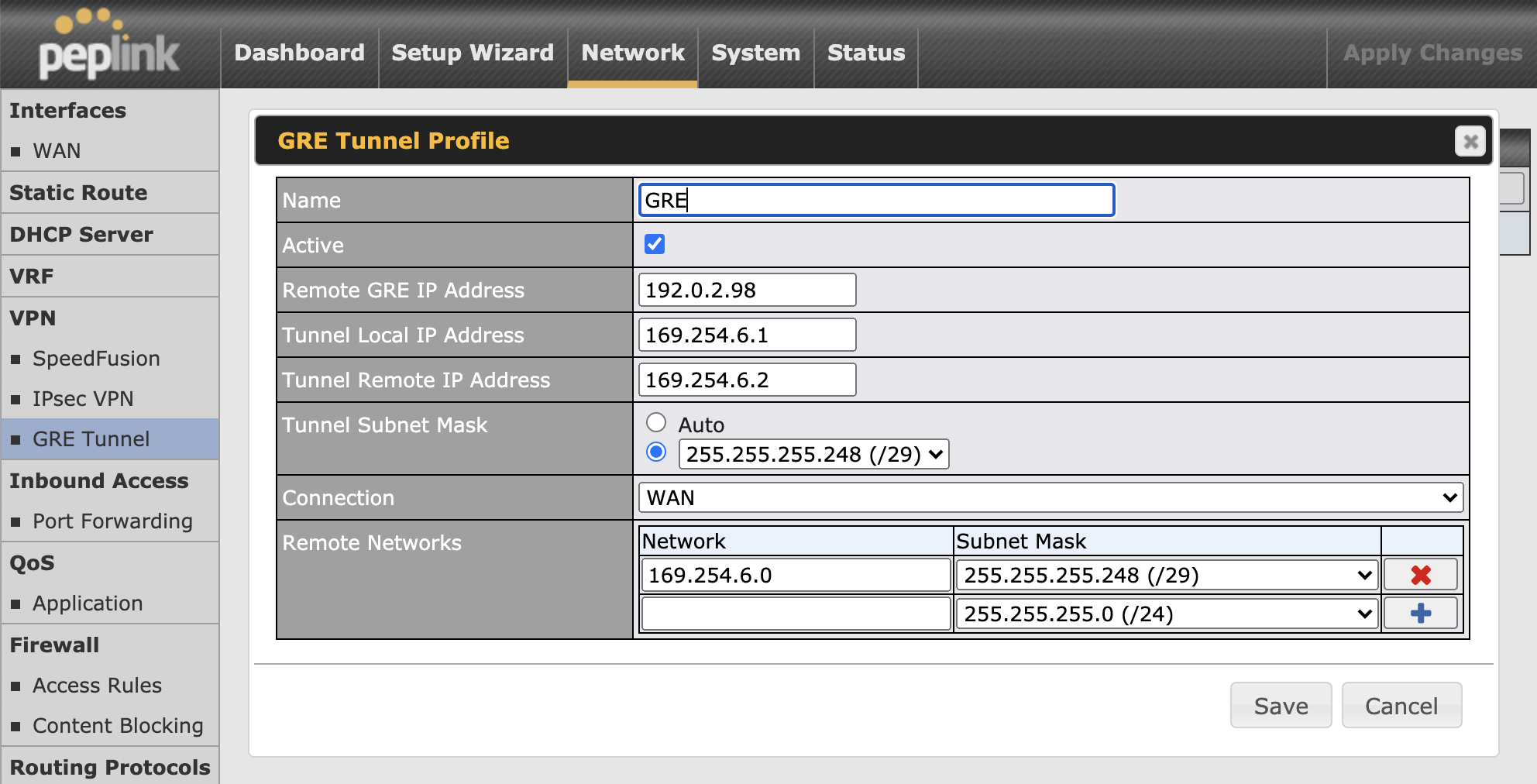
Afterward, head into the FusionHub, set up the GRE Tunnel by navigating to Network > GRE Tunnel, and clicking New Profile
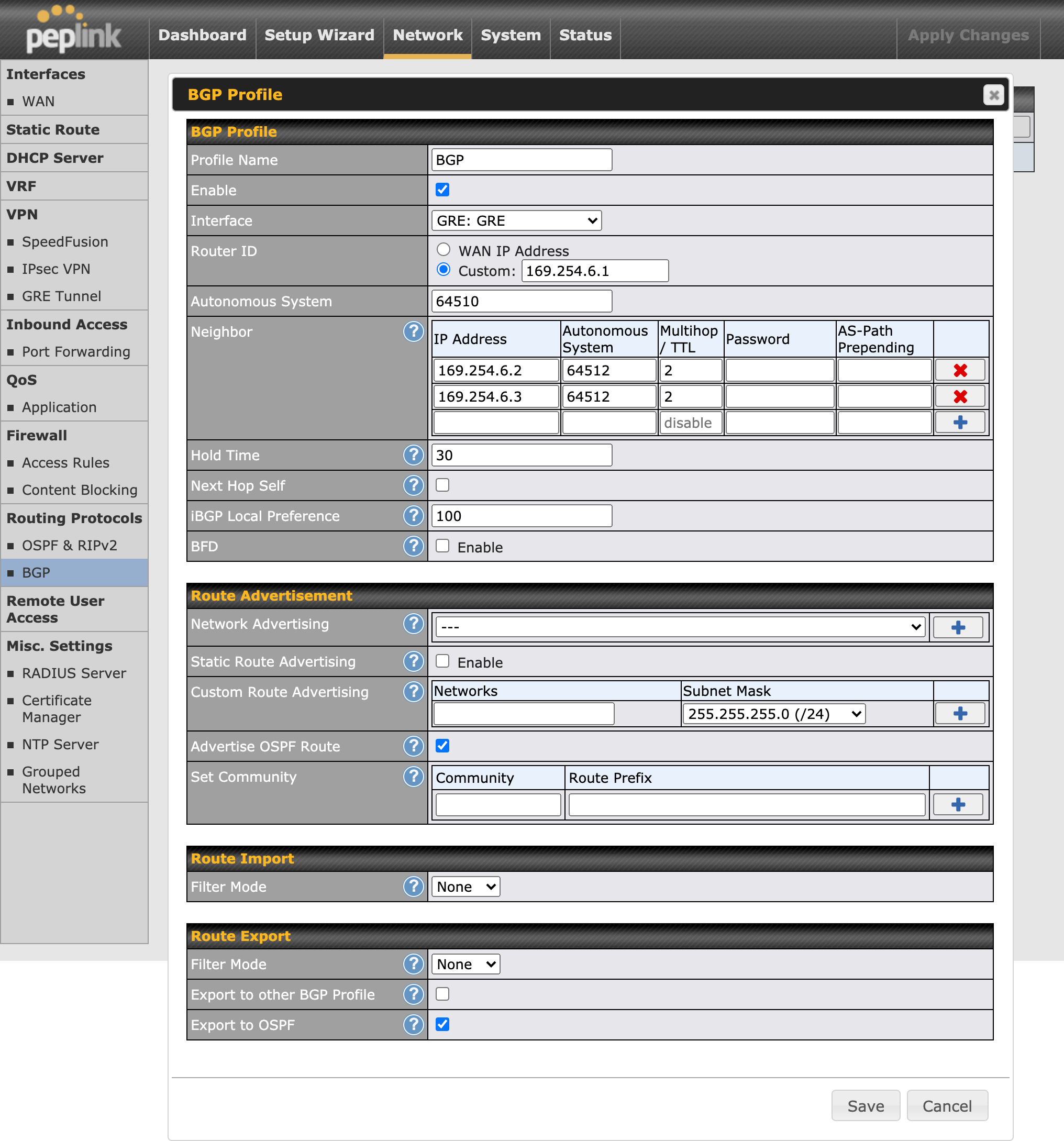
Finally, set up BGP by navigating to Network > BGP, and clicking New Profile
To allow communication between on-premises devices on SpeedFusion and AWS VPC, please enable “Route Advertisement > Advertise OSPF Route” and “Route Export > Export to OSPF”
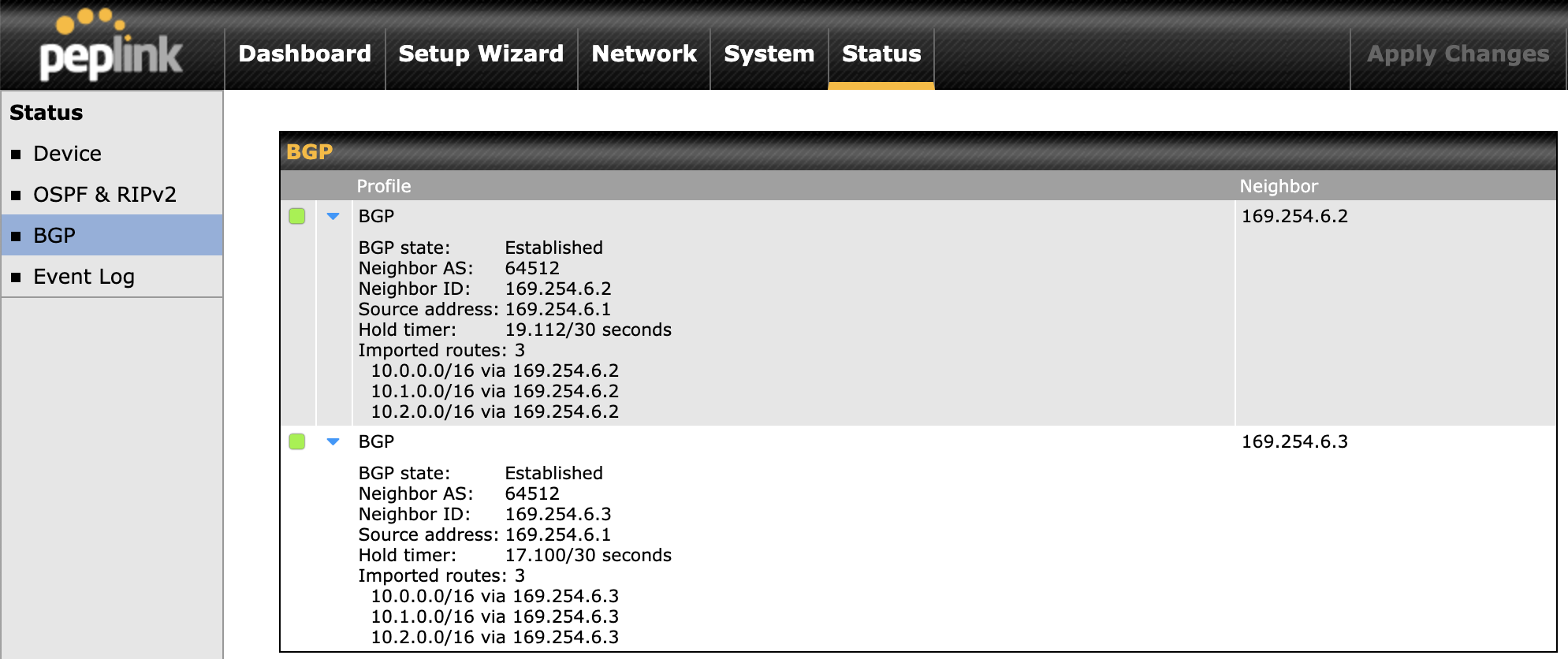
To verify the routes to the other AWS VPC, navigate to Status > BGP