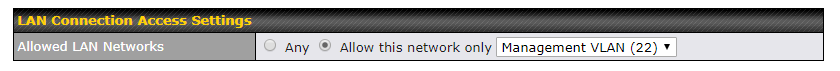
If you have multiple VLANs you can restrict web admin access to a single VLAN but this then means that the WebUi can only be accessed by a device on that same VLAN (so locally connected, or remotely over a Layer 2 VPN).
Firewall rules can’t block access to the webui either or restrict access to specific subnets.
I agree, we ought to have a access control list for the local web admin ui - the ability to add a list of subnets that can access it (either locally or over PepVPN).